WordPress on WordPress crime
 When you are a large content management system (CMS) that supports roughly 19% of the internet, people are going to come after you. Nothing invites hacking like popularity. It’s a large reason why years ago I always felt safe having a Mac. No one messed with it because way more people had PC’s.
When you are a large content management system (CMS) that supports roughly 19% of the internet, people are going to come after you. Nothing invites hacking like popularity. It’s a large reason why years ago I always felt safe having a Mac. No one messed with it because way more people had PC’s.
This is the case with WordPress. So many websites run on it that it’s worth it for hackers to jack it. Recently, they even used WordPress features to attack another very popular WordPress site (they wouldn’t say which one), according to the web security firm Sucuri.
From PC World:
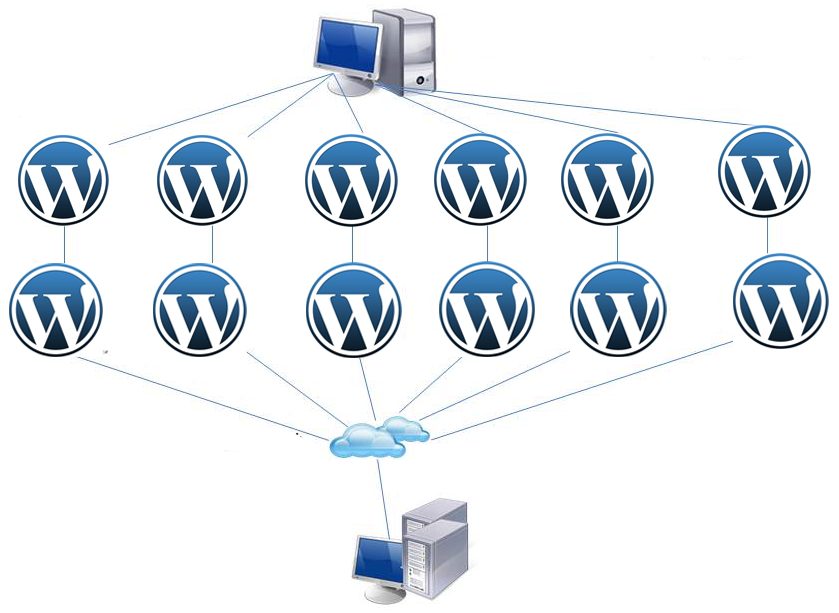
The attack exploited an issue with the XML-RPC (XML remote procedure call) implementation in WordPress that’s used for features like pingback, trackback, remote access from mobile devices and others, and brought back into the spotlight the denial-of-service risks associated with this functionality that have been known since 2007.
“Any WordPress site with XML-RPC enabled (which is on by default) can be used in DDoS attacks against other sites,” Sucuri CTO Daniel Cid said in a blog post.
DDos stands for distributed denial of service. Basically, when all of these sites send these pingbacks and other nonsense to that site, it interrupts service and users can’t get on the site.
Hooray?
The solution, of course, would be to disable the XML-RPC, but that would negate other important features, so that’s not a great option.
“I spoke to the WordPress team and they are investigating ways to minimize this issue, while still having the pingback functionality available (which is important for them),” Cid said.


